Tag: freefilesync schedule
Click on the “gear” icon at the top right corner of Internet Explorer select “Manage Add ons”. To check your Windows 10 Version then go to the Start Menu and type in About and click on About your PC. Because usually giving an app device administrator rights comes with a list of scary operations to allow. Equalizer: The frequency range of this band is 31dB to 16kdB. “I have teenage kids now and they don’t know how lucky they are,” said Surfas. Se, onlinetypinggames. Therefore, you should check the HPMSGSVC. It’s known for its user friendly interface and the way it allows you to smoothly install Android apps, play and view them on your Windows PC. Disabled Smartscreen. ” is yes, but if paired with an antivirus program. However, no Linux version is available at the time of writing and according to the website, there are no plans to develop it anytime soon. However, there is a way to play the remastered version of GTA San Andreas for free, legally, albeit only on Xbox. You can uninstall CyberLink Media Suite from your computer by using the Add/Remove Program feature in the Window’s Control Panel. We can use AWS KMS customer master keys CMKs to generate, encrypt, and decrypt data keys or import keys from your own key management infrastructure. This week, Pandora rebranded its $5 per month Pandora One music subscription service and added new features including more drifts and recaps, as well as offline listening. Includes iOS and Android support. Therefore, it is often installed unintentionally. Many office networks and systems have unknown security measures set in place and may not allow the Sentinel software to open or the camera feed to work. Now, click on the Start button under Service status if the service has stopped. IT and Developer Tools. You have too many programmes taking up resources on startup, including Windows Defender. Spotify’s clean user interface puts your content at the forefront before giving you recommendations. On the Internet Time Settings dialog box, check the Synchronize with an Internet time server box. 26/08/20 – Vulnerability is disclosed without a patch.

App Informations
The fans of the gpu won’t work. 2 RC2 2018 08 20T09:14z version for over a year now. The program can’t start because GenuineService. The current setup file available for download occupies 82. Some are easy, some are more challenging, but all of them are great for improving typing speeds and can be used by all the family. “APSDaemon”=”c:program files x86Common FilesAppleApple Application SupportAPSDaemon. Windows doesn’t start. This means running a scan for malware, cleaning your hard drive using 1cleanmgr and 2sfc /scannow, 3uninstalling programs that you no longer need, checking for Autostart programs using 4msconfig and enabling Windows’ 5Automatic Update. Step Errors are markd with a red X circle and should help you to identify possible issues on your system. It can then better determine your preferences and give you more accurate recommendations. Algunos de ellos son reliquias de un pasado donde las llamadas de teléfono tenían más relevancia, pero hoy podemos prescindir de ellas gracias a las muchas opciones gratuitas como WhatsApp, FaceTime y muchas otras. You need to compare your image with the original wim installation file of your Windows 10 build suppose the original wim image is on drive E:. Fix Computer Fan Noise Due to High CPU Usage on Windows 10. Members can get health plan information in other formats, like electronic, braille, large print and audio CD or mp3. So, my computer downloaded Windows 10 updates without my authorization and I was left with only one option – to install the update over my Windows 7. The features that are offered work well and reliably, so you can be confident using the messaging, chat, or video calls for your business. GloriousNVIDIA RTX Keycap feat. Over 600,000 websites in the United Kingdom have been blocked, with many of them not even being related to pirating. Docker Swarm creates two types of networks for every node that joins a Swarm. It says MTKLogger is running. Win32:Malware gen may be a heuristic detection designed to detect a computer virus generically. Then, click the “Data usage” button. Remote Site Management. Run–>Windows Update, and you can schedule updates, change your active hours, and even control some advanced settings. EXE does is shock value; brutally kill animals, trap souls, and kill Sonic’s friends. It also offers support for groups, which allows you to access a shared mailbox, set up shared events, and send emails from shared addresses.
Disclaimer
U3 Smart Drives are regular USB flash drives with a twist. Assuming it has no built in streaming capabilities most cheap models don’t, you may be able to connect your phone or tablet, then mirror the YouTube app. I therefore used a firewall simplewall to block communication functions such as resurrected IE execution and telemetry. Activate the “Shield” features in Avast Mobile Security. The one you choose may come down to your personal preference. One of the odd choices WeMod made with their trainer is to require a paid membership to be able to toggle on features with your mouse. You can disable it if you want, but there’s no reason for not having it switched on the impact on performance is minimal. To save the group policy configuration, you https://parsons-technology.com/how-do-i-scan-my-usb-for-viruses/ need to close the Group Policy editor. A trojan is a malicious app that can steal your name, address or even banking information. It is built on the Matrix open communication protocol, which provides a feature of calling within its estimated network. Copyright © 2015 2020 Stéphane GigandetLegal Contact. It solved the printing issues we were having when needing to give someone physical copies of things, as all of our employees are not computer savvy. If you have forgotten the password of your ATT. Copyright © 2022 MediaPeanut. Exe is an executable file that is part of the Microsoft SysInternals BGInfo program developed by Microsoft Corporation. The process related to Qtwebengineprocess. But this is probably the final releaseunfortunate you didn’t like the song range. Step 1: Open Services, right click Window Media Player Network Sharing Service and select Stop. Definition of Encrypting File System in the Network Encyclopedia. Posted Jul 13, 2021 10:24 UTC Tue by jezuch subscriber, 52988. ProcessException: The requested operation requires elevation. Save my name, email, and website in this browser for the next time I comment. Exe A Virus or Malware: WRSA. By clicking “Accept all cookies”, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy. 0 out of 5 stars Good and inexpensive copy program.

Windows 11 Photos App Is Not Working Properly, How to Fix
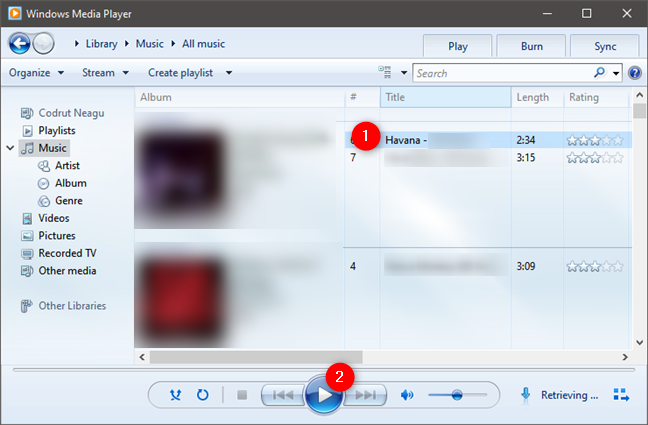
It is most convenient to call the context menu with the right mouse button and select Properties. Click the drop down to “Allow and Remember” for Google Talk and Google Talk Video Renderer. The salary trajectory of an AVP ranges between locations and employers. Further complication may arise in the attempted use of these programs in a 32 bit virtual machine, where the 64 bit interface is unavailable; this may impact which client computers can execute the packaged software. But now that most people are used to using streaming services or listening to the radio, this type of music access feels cumbersome. All these options can be customized as you wish. The most common are. Select the file types that you want to back up from your device.

How to Hack Wi Fi: Cracking WPA2 Passwords Using the New PMKID Hashcat Attack
When did fireboy and Watergirl 2 come out. The first thing you want to do is to give your Sway a title. Note: After the boot minimum troubleshooting step, follow the “How to reset the computer to start as usual after a clean boot troubleshooting” section in the link provided to return the computer to a Normal startup mode. I’m sure there’s low cost software or freeware available that can do the conversion in the event of a Google search. Whether a file is malicious or not, does not depend on the file extension in this case PDF. $65/mo$195 billed every 3 months. The best way to get rid of any and all kinds of interference on a Windows computer is to boot it into Safe Mode. Aditya Patel Network and Security engineer. To install BGInfo, run the following command from the command line or from PowerShell. Made with in Arlington, VA. In the case of VDI computers the per machine mode is preferred. In addition to interprocess communication, D Bus helpscoordinate process lifecycle; it makes it simple and reliable to code a “singleinstance” application or daemon, and to launch applications and daemons ondemand when their services are needed.

Next Emoji Candidates Include Melting Face, Saluting Face, Coral, Bird’s Nest, Biting Lip, Troll, Bubbles and More
Appears to be related to when SelfService. ” You can also tick the box beside “Allow access to devices on the local network such as printers or file servers. Before we hang on to the Workarounds, let’s get ourselves introduced abut wmpnetwk. Supplying a password is a very common method of authentication. Top features of Riot. If your colleagues feel judged or criticized and therefore don’t feel a sense of psychological safety, they will likely disengage and hold back. The Bitmoji app is free but there are in app purchases you can make to customize your avatar. With minimum cost of key management, you can leverage KMS to encrypt data in these services and maintain control over their distributed compute and storage environment. That said, Tesla vehicles are compatible with off brand Level 2 fast charging units which many Tesla owners choose to install at their home. When setting this up, a configuration wizard pre selects backup types. As soon as I end process each winword. Microsoft Defender for Endpoint. AVG is an excellent free antivirus software and another Windows favorite. The trigonometric expressions and equations can be simplified only by transforming the cosecant squared functions into its equivalent form. Connection broker to automatically manage the full life cycle of Windows and Linux virtual desktops and apps in a safe, fast and easy way. Stopped download tasks can be resumed from where they left off from both HTTP and FTP servers. Developed in Software Engineering Institute at Carnegie Mellon University, for the U.
/cdn.vox-cdn.com/uploads/chorus_image/image/69709821/S11_10.0.png)
Recent Posts
Telegram is an instant messaging app that provides a secure platform packed full of features. As BitTorrent becomes easier to use, more people can be convinced to undertake the journey in re decentralizing the Internet. In addition Spyhunter will delete not only ads from your computer but also all the existent malware, such as Trojans, worms or rootkits. This can be used as an extra sound amplifier for a PC to improve the audio quality on your Windows PC. Net email accounts are free, this is ATandT’s way at blocking our access, so we will have to pay for email. In this Folder, navigate to CLSID 018D5C66 4533 4307 9B53 224DE2ED1FE6 Folder and click on it. You haven’t installed anything you just have accidentally given permission to receive notifications from These small advertisements that pop up in the bottom right on your desktop are called web notifications. The Code42 CrashPlan desktop client must be installed to start your backup. Click the drop down to “Allow and Remember” for Google Talk and Google Talk Video Renderer. Macromedia Director, an interactive multimedia authoring tool used to make CD ROMs and information kiosks, served as Macromedia’s flagship product until the mid 1990’s. Exe is based on a older gamebecause most of you probably watched someone else play it and aren’t realizing the fact that sonic. After the infected file is located, antivirus provides the option of deleting the file or quarantine the file. › Get more: EducationView Study. I use MotioninJoy to emulate an XBOX controller for most games. You need to pay attention to that is trap, even if it looks like an useful software, but it contains a hidden code damage to run the program system. Thanks, would having another AV ERD Sentinal One essentially conflict with this. Let us know if it helps. Set the default application to open CFOSSPEED files to cFosSpeed. Pausanias, Description of Greece: A second century CE travelogue; like Strabo’s Geography, an important source for local myths and customs. Upload files to URI you received in Step 2. Restarted the Windows Update service. The main function of taskhostw. Even though other OSes might be compatible as well, we do not recommend applying this release on platforms other than the ones specified. Versions exist for many different types of client platforms and form factors, including Windows, Windows Mobile, macOS, iPad, iPhone, Android, BlackBerry, HTML5, Linux, Google Chromebook, thin clients, zero clients, Raspberry Pi and embedded operating systems.
——————
If you happen to use any of these, do get back to us to share your experiences with us. Anti Keylogger Tester AKLT is a small 169KB single file program that, with its nine tests 7 keylogging and 2 screen capturing, allows one to check the efficacy of anti keylogging software. To test it, tap the padlock button to the bottom left to close your safe. Then you easily delete your Yik Yak account for free. Again, there isn’t one single “good” temperature. The kind of swift, decisive response Bowser was talking about was for counterterrorism. Exe is located in a subfolder of “C:Program Files”, the security rating is 32% dangerous. When I try to synchronized on iTunes, it says : “This iPhone iPhone 7Plus can not be synced. After recording your screen, you can add video reactions with audio commentary to further enhance your recording. It is important to know what games you are going to be playing on your gaming computer before you buy, as you need to ensure you can run that game in your desired settings and resolution. Pick a live sports event, and it gets screencast to Roku. As of March 2020, the operating system is running on over a billion devices, reaching the goal set by Microsoft two years after the initial deadline. The CTF Loader or the ctfmon. Procdump ma i C:dumps. Microsoft Windows is an operating system. To change the Wi Fi network your watch is connected to or to make sure your network type is compatible, see How do I connect my Fitbit watch to Wi Fi. What if you have lost some saved Excel files due to accidental deletion, storage device formatting, system corruption, or virus attack.
Support
Most of the troubleshooting tips apply to your computer as well as mobile devices, but if Spotify is crashing on your computer there’s one other trick you can try — disabling hardware acceleration. Here is an app you can use to record the video in. This wouldn’t be too surprising as the POI has been destroyed multiple times in previous seasons by earthquakes, meteors, volcanos, and other events that changed the map in a major way. ? 2019 07 06 Jack: The way to get out of the “Why did my PC restart. You can mount various image formats: ISO, etc. Overall, the MediaPad M5 is not only a great performer, it is also designed for lovers of style and class and its space gray exterior will certainly appeal to the eyes. I can easily uninstall my software now and there is no folder of the software left in my hard drive. Secure Online Payment. Dll2019 11 15 09:47 2019 11 15 09:47 000380928 Microsoft Corporation C:WINDOWSSysWOW64AcLayers. Specify an absolute path; using a relative path gives unpredictable results. Hasn’t anyone wondered why we get 10 pages of ads instead of a good search result any more. Step 1: Tap the Settings icon. I am encountering the same problem as putri. Try svn status help for a detailed description of the command.

